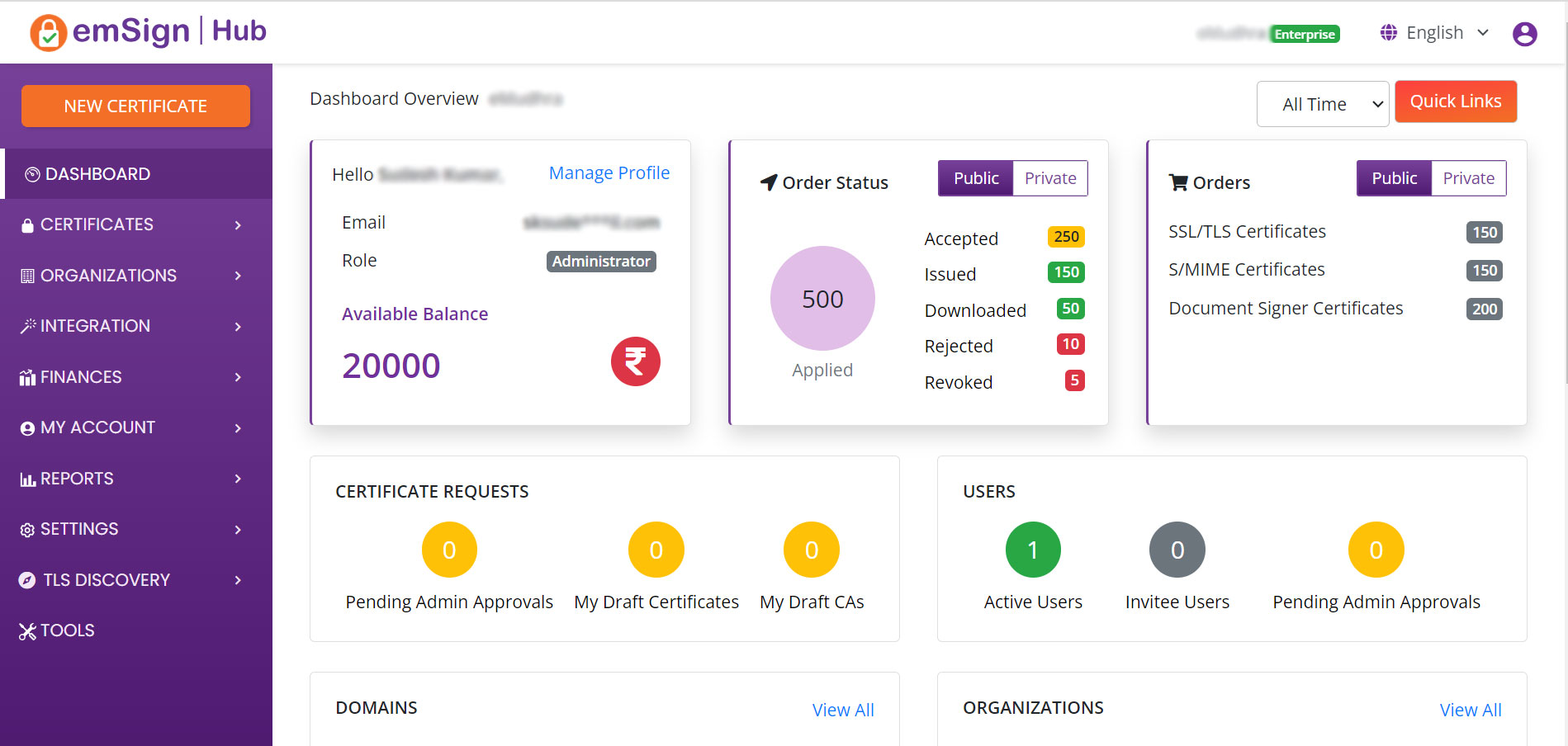
emSign Hub comes with discovery capabilities out of the box to help you identify your vulnerabilities and ensure that they are addressed quickly and easily. emSign Hub comes with a single free agent that can allow you to discover certificates in your network. Additional agents for complex environments can be procured or bundled with your emSign Hub package.

These are used for securing network connections, typically for web servers (HTTPS), but they can also secure other types of network connections. They confirm the identity of the server to the client and enable the client and server to establish an encrypted connection
These are used for signing and encrypting email communication. They allow the recipient of the email to confirm the sender's identity and ensure that the email has not been tampered with during transmission

These certificates are used for digitally signing documents to verify the sender's identity and ensure the document's integrity. The certificate confirms that the document originated from the claimed sender and has not been tampered with since being signed

These are used to authenticate Internet of Things (IoT) devices, ensuring secure data transmission. IoT certificates confirm the device's identity, encrypt data in transit, and help maintain data integrity. They also enable device-level authorization, controlling the access of a device to specific resources within the network

These are used for signing software code. The purpose is to authenticate the source of the code and confirm that it has not been tampered with since being signed
These certificates are utilized in MFA processes to enhance security for users, machines, and devices. They add an additional layer of security by requiring more than one form of verification, thereby ensuring that the entity seeking access is indeed authorized
Certificates are great in protecting your Environment and encrypting traffic and data. But they only remain great if you make sure you renew them on time. Moreover, there's a chance that your organization has got a bunch of Certs lying around that may be dated, with inadequate encryption strength, simply waiting as bait to the next cyberthreat that hasn't taken place yet.
CertiNext, eMudhra's CLM is pre-integrated with emSign Hub to help you identify vulnerable Certs and Certs that are about to expire. But with CertiNext, identification is just the start. CertiNExt allows you to configure workflows and policies that can automate Certificate renewal to ensure zero downtime. With optional Key Management capabilities, you get a one-stop solution not just to uptime, but also encryption management across your organization.
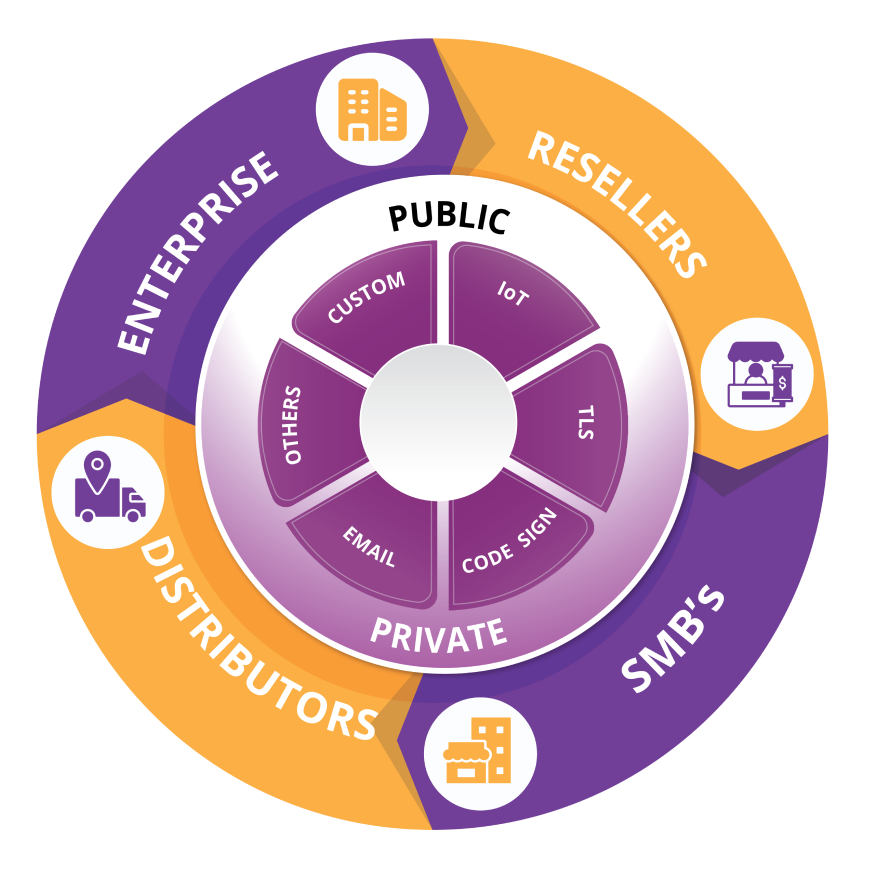
Enterprise PKI helps secure digital transactions, confirm the identities of devices and users, and maintain the integrity and confidentiality of information in your organization.
The total cost of ownership varies depending on the number of certificates needed, administrative requirements, and the payment model (e.g., pay-as-you-go, prepaid account, or unlimited issuance license).
Bulk purchasing provides significant volume discounts, reducing the cost per certificate compared to purchasing individual certificates.
By streamlining processes like issuance, revocation, and renewal of certificates, you can minimize the time spent on certificate administration.
These integrations help automate the distribution of certificates, reducing manual efforts and making the provisioning process more efficient.
Centralized control allows you to manage all certificates and user activities from one place. This includes actions like revoking, renewing, reissuing, and canceling certificates.
Through centralized control, you can set permissions determining who can issue certificates, the types of certificates that can be issued, and the domains or entities they can be issued to.
Yes, a single account can be used to manage the certificates of multiple departments or business entities.
IoT device certificates authenticate the device's identity, encrypt data in transit, maintain data integrity, and provide device-level authorization, ensuring secure IoT operations.
MFA adds an extra layer of security by requiring more than one form of verification. This ensures that the entity seeking access, whether it's a user, machine, or device, is indeed authorized.